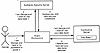
Exhibit 1. Kerberos Authentication Process
| Previous | Table of Contents | Next |
Ray Kaplan
Joe Kovara
Glen Zorn
One of the most significant problems in securing distributed systems is authentication. This is, ensuring that the parties to a conversation — possibly separated by a wide area network and traversing untrusted systems and communications paths — are who they claim to be. Kerberos is currently the de facto standard for authentication in large, heterogenous network environments.
Kerberos has been in production for more than six years in one of the world’s most challenging open systems environments — Project Athena at MIT.1 Kerberos is the backbone of network security for Project Athena, where it protects more than 10,000 users accessing thousands of workstations and hundreds of servers. Kerberos protects thousands of sessions and tens of thousands of mail messages per day. As such, Kerberos is arguably the best-tested, most scrutinized authentication protocol in widespread use today.
1Project Athena is a model of “next-generation distributed computing” in the academic environment. It began in 1983 as an eight-year project with DEC and IBM as its major industrial sponsors. Their pioneering model is based on client-server technology and it includes such innovations as authentication based on Kerberos and X Windows. An excellent reference — George Champine, MIT Project Athena, A Model for Distributed Campus Computing, Digital Press, 1991.
HISTORY OF DEVELOPMENT
Many of the ideas for Kerberos originated in a discussion of how to use encryption for authentication in large networks that was published in 1978 by Roger Needham and Michael Schroeder.2 Other early ideas can be attributed to continuing work by the security community, such as Dorothy Denning and Giovanni Sacco’s work on the use of time stamps in key distribution protocols.3 Kerberos was designed and implemented in the mid-1980s as part of MIT’s Project Athena. The original design and implementation of the first four versions of Kerberos were done by MIT Project Athena members Steve Miller (Digital Equipment Corp.) and Clifford Neuman, along with Jerome Salzer (Project Athena technical director) and Jeff Schiller (MIT campus network manager).
2Needham, R.M. and Schroeder, M., Using encryption for authentication in large networks of computers, Communications of the ACM 21 (December 1978), pp. 993–999.
3Denning, D.E. and Sacco, G.M., “Timestamps in key distribution protocols, Communications of the ACM 24 (August 1981), pp. 533–536.
Kerberos versions 1 through 3 were internal development versions and, since its public release in 1989, version 4 of Kerberos has seen wide use in the Internet community. In 1990, John Kohl (Digital Equipment Corp.) and Clifford Neuman (University of Washington at that time and now with the Information Sciences Institute at the University of Southern California) presented a design for version 5 of the protocol based on input from many of those familiar with the limitations of version 4. Currently, Kerberos versions 4 and 5 are available from several sources, including both freely distributed versions (subject to export restrictions) and fully supported commercial versions.
FUNCTIONAL OVERVIEW
Kerberos is an authentication protocol that has been built into a system that provides networkwide security services. Kerberos can solve many of the security problems of large, heterogeneous networks, including mutual authentication between clients and servers. The basic idea behind Kerberos is that a trusted third party (the Kerberos security server) provides a means by which constituents of the network (principals) can trust each other. These principals may be any hardware or software that communicates across the network. In addition to authentication, Kerberos offers both privacy and integrity for network messages.
There is considerable detail in describing how Kerberos works, and the actual exchanges that take place over the network are a bit complicated. However, the basic idea is quite straightforward and follows this five-step process:
Exhibit 1 illustrates how this works.

Exhibit 1. Kerberos Authentication Process
SCOPE OF SECURITY SERVICES
In his treatise on distributed systems security, Morrie Gasser4 categorizes the security services that a distributed system can provide for its users and applications as: secure channels, authentication, confidentiality, integrity, access control, non-repudiation, and availability.
4Gasser, M., Security in distributed systems, in Recent Developments in Telecommunications, North-Holland, Amsterdam, The Netherlands; Elsevier Science Publishers, 1992, pp. 145–228.
| Previous | Table of Contents | Next |