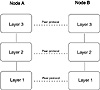
Figure 4.1 A simple three-layered network model.
| Previous | Table of Contents | Next |
So far you have seen that I&A and access control for systems are not enough for a complete security solution. You learned that intrusion detection is needed to monitor your systems because I&A and access control, even when augmented with other products, still leave your system vulnerable to attacks. Intrusion detection will not prevent these attacks, but it can help you detect trespassers when they enter your site. If your responses are configured properly, an IDS can help stop hackers before they get too far.
The last two chapters dealt with I&A and access control mostly from the perspective of a single computer without network connections. Now that you understand the basic issues in I&A and access control, let’s move forward into network security. As the first section shows, network security is a bit more complicated because it introduces new sources of threats.
Next, you’ll examine the important entities in network security. When you examined I&A in the basic stand-alone model, the user was the chief entity of interest. The user was represented by subjects such as processes or threads that operate on the user’s behalf. In access control decisions, the subject was represented by a set of UIDs and GIDs. In some network communications, these credentials are still important, but new entities must be addressed as well. Examples of other entities include network nodes and software processes that communicate over the network. Therefore, in this chapter, you will see how I&A and access control are implemented for these entities, too. You also will learn about the weaknesses in some widely used Internet protocols, although many improvements to these standards are being implemented in commercial products today.
Like stand-alone systems, network attached systems must meet the three security goals identified in Chapter 1 (confidentiality, integrity, and availability). Stand-alone systems primarily use a combination of I&A and access control to meet these three goals, although cryptographic methods are sometimes employed to protect files on a disk. As you move into the network space, you will find that these same basic mechanisms—I&A and access control—are equally important for ensuring network security. However, you eventually will see that cryptography provides the best security for network communications.
Because one of the most commonly used access control products for networks is the firewall, some time will be spent describing firewall architectures and features. As in the case of I&A and system access control, you will see that firewalls still do not complete the security picture for your site. Knowing the limitations of firewalls and other network security techniques will complete the foundation necessary for understanding the need for intrusion detection.
One of the reasons that network security is harder is because the channel over which two entities communicate may be unsecure. On a stand-alone system, when two programs want to exchange information, the operating system provides a variety of secure mechanisms. The programs can communicate using shared memory, message queues, pipes, or files. All of these techniques are handled by the operating system, which the programmers assume to be trustworthy.
When two programs need to communicate across a network, the assumption of trustworthiness is not always valid. By default the Internet does not provide a secure network transport. Because the network is open to just about anyone, a number of threats arise—threats that are not seen in stand-alone systems. One of the best ways to visualize why these threats occur is by looking at an abstract model of networks using a layered architecture.
The ISO model of networking defines seven layers in the network stack. Widely deployed network technologies, such as the Internet Protocol (IP), Novell’s IPX, Microsoft’s SMB, and IBM’s SNA, all implement variations on this seven-layer model. The basic ideas behind the layered model are simple.
Consider an example in which two computers want to communicate with each other over a network. At the lowest layer of the network is the Physical layer on which the electronic impulses flow. At successively higher layers, communication protocols are stacked on each other. Each layer has a very specific purpose and plays a well-defined role in that it provides services that layers above and layers below need. The main theme here is encapsulation. A layer is responsible for providing a certain set of abstractions in the form of interfaces. Think of a given layer as providing services to the layer above and services to the layer below. Layer N provides services to layer N-1 and to layer N+1. Breaking the model into layers simplifies both its architecture and its implementation.
Because information flows in both directions in the network stack, layer N has responsibilities that include sending information to and receiving information from layers N-1 and N+1. Smaller numbered layers typically begin at the physical network layer, and numbers increase as you move up the stack. Also, at each layer in the model is a conceptual communication channel that exists with the peer (same numbered) layer on the other network node. That is, layer N on node A is communicating with layer N on node B even though the data they exchange must actually pass through lower layers on the respective nodes.
Consider a simple three-layered model shown in Figure 4.1. In this example, Layer 3 represents an application program running on the system, Layer 2 represents a network software layer, and Layer 1 represents the physical network layer. For network packets to be sent at Layer 1, a restriction may indicate that each packet be a maximum of 10-bytes long. Any information sent to Layer 1 from Layer 2 must be fragmented into 10-byte packets. If Layer 1 of node A receives a packet longer than 10-bytes, not only must it be broken apart to be transmitted at the Layer 1 level, but some type of meta-data must be added to the packets so that they can be reconstructed by Layer 2 on the receiving system B. This meta-data is commonly referred to as a packet header.

Figure 4.1 A simple three-layered network model.
| Previous | Table of Contents | Next |