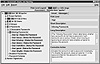
Figure 7.2 Example output from an S3 scan.
| Previous | Table of Contents | Next |
File Integrity Checker
Like many other security products, S3 includes a facility for computing cryptographic signatures for selected files. The database of signature-file pairs is stored and examined at future intervals to detect possible Trojan Horses. An MD5 signature is computed from various file attributes. Stored in the database with the file name are its MD5 signature, permissions, owner, group, and size. If any of these parameters change, the next file integrity scan will generate an alert. Shipped with each installation is an OS-specific baseline file containing a predefined set of file names to monitor with the integrity checker.
Results and Reporting
Scan outcomes are stored on the local node if the scan is local and in separate per-node subdirectories on the central engine for distributed scans. Results files are not in human readable format and must be analyzed with either the GUI, CLI, or an HTML browser. The first level detail output indicates the number of high-, medium- and low-risk vulnerabilities found along with informational and error messages. Failing to complete a scan due to network faults would generate an error condition.
In the GUI, results can be examined by node, by group, or by vulnerability type. Users familiar with file system browsers such as NT Explorer easily will adapt to the hierarchical reporting user interface shown in Figure 7.2. In addition to sending output to the screen, S3 optionally generates ASCII, comma-separated, and HTML reports.

Figure 7.2 Example output from an S3 scan.
Vulnerabilities Scanned
S3 organizes its vulnerability database hierarchically within several different categories, including:
The entire set of scanned items is too long to list and describe in detail here. A summary of scanned weaknesses is given in Table 7.1. You should consult the ISS Web site www.iss.net for the most current list.
| Vulnerability Scanned | Description |
|---|---|
| Password File | Blank lines in password file; Improper characters in password file |
| Trusted hosts | hosts.equiv and .rhosts for system or users; .shosts files for ssh, and.netrc files |
| RC files, crontab, user-owned files, and printcap | Improper ownership and permissions for files; Bogus path names in entries; Improper settings for programs invoked by cron, RC scripts, printcap, and user profiles; Improper symbolic links |
| External and local file system | World-readable and world-writable file system exports; Wrong owner or permissions on critical system files and programs; SUID and SGID programs; Unusual file names; Hidden files and directories; |
| Internet services | HTTP daemon user and group account security (no root or Administrator access); Incorrect permissions on directories in the Web virtual file tree; Unrestricted FTP access; Unsecure services enabled—tftp, chargen, fingerd, FSP, and others; Ownership and permission problems for programs; Bogus path names in configuration files |
| Sendmail | Old version checks; VRFY and EXPN enabled; Mail aliased programs; Authentication warnings; Permissions and ownership of mail spool directories |
| Software bugs | Checks for known vulnerable programs to see whether patches have been applied; extensive checks for buffer overflow attacks |
| Users and groups | Invalid UIDs and GIDs; Accounts with root privileges; Duplicate UIDs and GIDs; Invalid home directories or initial programs; Dormant accounts; Unused accounts; Weak, missing, or easily cracked passwords; |
| Netscape browser settings | Java and JavaScript enabled; POP mail password |
| Network adapter enabled for promiscuous mode | Checks for sniffer activated |
Internet Scanner
The ISS Internet Scanner looks for a number of system and network weaknesses in your nodes. The model is remote scan from a central node, and all results are centrally captured because the scan is only running on one node. Depending on the options purchased, Internet Scanner will look for Web, firewall, common, and system weaknesses. The possibilities are controlled by an electronic license key. The initial Internet Scanner screen is displayed in Figure 7.3.
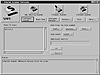
Figure 7.3 Main screen for Internet Scanner.
Vulnerabilities Checked by Internet Scanner
Some of the same problems that S3 reports also are discovered by Internet Scanner, although in a different way. For example, a world-writable NFS exported file system is a potential security vulnerability (depending on the security policy at your site). S3 detects this vulnerability by looking at the currently exported file systems or by examining the NFS exports configuration file in case the file is not currently exported for mounting. Internet Scanner checks for this same vulnerability by either attempting to mount exported file systems with read-write access or by querying the list of exported file systems on a node using the showmount command.
Telling Internet Scanner which vulnerabilities to probe is straightforward. Figure 7.4 shows a screen image for IP spoofing scan options for the Internet Scanner. As you can see, the interface is slightly different from S3. Choices are indicated by setting radio buttons and entering optional data in fields. In Figure 7.5 you see some of the possibilities when the target of the scan is a Web server. Note the inclusion of the phf.cgi attack. The List CGI button causes ISS to check for the test.cgi hack. You can select different scan intensities-full, heavy, medium, and lite. A custom configuration is easily defined as shown.
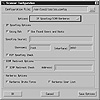
Figure 7.4 Configuring IP spoofing options in Internet Scanner.
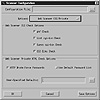
Figure 7.5 Web server scan options in Internet Scanner.
Following is a list of the vulnerabilities that are potentially scanned. Not all options are always available. Firewall and Web specific items are supported only if you have purchased the appropriate license. See the ISS Web site for the most current list.
| Previous | Table of Contents | Next |