
Figure 9.3 RealSecure’s initial management panel.
| Previous | Table of Contents | Next |
An Infoworld test reported in the May 4, 1998 issue rated products as follows:
The study by the Infoworld team announced a suite of 16 well-known network attacks that they tried against the products. Only NFR caught all of the attacks. The team used the scripting language, with help from Anzen, to build tests that do the following:
The chosen IDS were challenged with attacks such as the following:
In all, 23 attacks were attempted individually, with two combinations of attacks completing the full suite of 25. (Some of the 16 attacks have more than one variation that is how one arrives at 23 individual attacks.)
A three-way tie for first place exists between IBM/NetRanger, RealSecure, and NFR. Abirnet fell into last place for three main reasons—it lacks systems management; it does not have specific IDS reports; and it failed to detect 7 out of 25 attacks. The reviewers nonetheless liked many of SessionWall’s features. The next few sections focus on the three IDSs that tied for first place.
As noted previously, NetRanger is a passive network monitor that is offered with an NSC router or as a stand-alone product on a UNIX box. Hierarchical secure remote reporting between sensor stations and a console is one of the key features of NetRanger. The WheelGroup also reports that NetRanger is more scalable than any other network IDS. NetRanger also can detect session hijacking—something that other network IDSs do not claim.
NetRanger not only detects events but also responds to them as well. Shunning IP addresses for an interval of time is one of the operations that NetRanger can send to the NSC router if you are running that combination. As you might expect, a wide range of response options are available including pager notification, e-mail, and pop-up alerts. Logging and reporting are standard features.
NetRanger allows scanning for administrator-defined strings in network packets—a feature that other network IDSs must soon provide. However, it is not a trivial task to add your own attack signatures to those already supported by NetRanger. This shortcoming is shared by many IDSs.
IBM’s Emergence Response Center offers a fee-based service with NetRanger. Instead of staffing your own team of security experts, you can use IBM’s strength in this area. A network operations center is staffed 7 × 24, and a specific expert is assigned to your account. When an event is detected, IBM’s security experts notify you and help you respond to the event. Up-front planning and response policy design also are available. As hackers become more sophisticated, outsourcing your network intrusion detection seems attractive because you may not be able to staff and maintain your own center of competency.
One final note about NetRanger is worth mentioning. Some of the founders and technical leads for the WheelGroup have worked at the Air Force Warfare Information Center and at the NSA. With contacts like that, it’s not surprising that a number of government sites depend on NetRanger for network intrusion detection. You know NetRanger has been tested substantially in the field.
ISS is already the market leader in scanning tools with SAFESuite. RealSecure is a widely used network IDS that complements ISS’s other offerings. Like NetRanger, RealSecure supports remote sensing stations, called engines, that report to a central console. Naturally, communication between engines and the console are cryptographically protected using a shared pass phrase. Figure 9.3 shows the initial panel for RealSecure.

Figure 9.3 RealSecure’s initial management panel.
Monitoring and response options can be customized for each engine. Recall from the previous discussions that your site should have one monitoring engine per subnet (possibly more for performance gains). In Figure 9.4, you see some of the attack signatures that can be configured by node in RealSecure. As before, a comprehensive list of attacks detected is best obtained from ISS because the product is updated regularly.
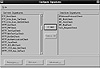
Figure 9.4 RealSecure attack signature configuration.
RealSecure also supports a playback mode, which can be used to dig through the network traffic looking for problems. In playback mode, the product does not run attack signature recognition on the playback traffic. This feature probably will be fixed in the near future. Once activated, the console begins receiving data from the remote engines. You can choose from a number of different views on the console including by node or by event severity (high, medium, or low). Data from the engines is logged, and a variety of reports are possible.
A number of different response options are available, including killing the offending network connection by sending a RST packet. Figure 9.5 gives a snapshot of how one might configure response options in RealSecure. Templates that declare signatures to use and how to respond to events can be applied to different engine nodes. Notifying an administrator is supported as a response along with the more aggressive socket kill option.
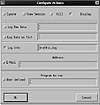
Figure 9.5 RealSecure response configuration.
RealSecure runs on UNIX and NT platforms. The engines and console can run on different OS platforms, too. Regardless of the platform on which the engine is running, it can detect specific attacks against TCP/IP, NT, NETBIOS, and UNIX. For example, even if the engine is running on an NT workstation, it can detect someone trying to exploit the old AIX “rlogin -froot” bug.
ISS also relies on its X-Force team of security experts to find new attacks and create (or adjust) signatures. Discoveries can come from the X-Force’s own research or from contacts that it has with the underground. ISS is well known for its NT expertise, with Microsoft often working closely with X-Force team members.
| Previous | Table of Contents | Next |