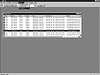
Figure 10.2 Event notification and responses in eNTrax.
| Previous | Table of Contents | Next |
eNTrax provides two IDS capabilities in a single tool. Because the Target Service is running on each node, local vulnerability assessments can be carried out. You can get this same type of function with ISS SAFESuite for NT or the Kane Security Analyst (KSA). The other IDS function provided by eNTrax is attack signature recognition. Most hacker attacks recognized by eNTrax are single events today, but work to build more complex attack patterns is in progress. Remote scans against target nodes are not part of the tool today.
An administrator typically would use eNTrax as follows. First, an assessment of the targets is requested from the console to look for security weaknesses. The Assessment Manager generates reports on the strength of a computer’s security. With this information, the administrator can improve the security holes that currently exist. The next step is to create an audit policy that effectively provides the capability to monitor user activities. eNTrax provides an Audit Strategy Tool component that simplifies creation of an audit policy. In addition, eNTrax ships with predefined audit policies, which can be modified as needed to suit the individual needs of an organization.
The third step is to distribute the audit policy to target computers. eNTrax provides a Target Manager that facilitates the distribution of audit policies to all target computers. After configuration is completed, the monitoring portion of eNTrax kicks into high gear. The Target Service residing on the target sends the local event log back to the Command Console for processing. Events are processed in pseudo real time with a configurable interval.
eNTrax is equipped with more than one hundred activity signatures to help identify attacks. Activity signatures are events or event sequences for which an alert is issued. Like many other IDS vendors, Centrax actively monitors the appropriate newsgroups and hacker resources to keep current with new attacks.
Analysis at the console consists of passing the event log through a detection engine that looks for attacks. Results are reported on the console and stored in a database. When an event is displayed on the console, administrators are notified of activities that appear suspicious. Other alert facilities include SNMP, pager, and e-mail notification. In a network operations center with personnel monitoring the console, the operator will look at the alerts and determine the appropriate action to take. eNTrax enables an administrator to assign priorities to events. This feature is useful because it lets the site decide which items are of high, medium, or low interest.
As noted before, responses include shutting down the user’s machine, killing the login session, or disabling the login account. Automated responses to alerts can be configured in advance. The response is applicable to the entire set of targets that the console controls. An enhancement would be to permit more granular responses, such as varying countermeasures by user or by target. Figure 10.2 includes a snapshot of the event notification screen and a pull-down menu for responses.

Figure 10.2 Event notification and responses in eNTrax.
To further enhance security, eNTrax provides a Report Manager with which an administrator can generate extensive reports of user or target node activity. These investigative reports provide a look at who did what, when, and how. Information such as this helps track down potential misuse and can pinpoint damage that has occurred. A sample report is shown in Figure 10.3. Useful trend reports also can be generated from historical data.
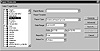
Figure 10.3 Sample report from eNTrax.
ISS SAFESuite and RealSecure for NT
ISS has a very concentrated team of NT security experts. Some of the developers there once worked on the implementation of NT security for Microsoft. It is even rumored that Microsoft’s Web site and internal IT infrastructure are pilot test networks for new releases from ISS. In earlier chapters, you read about products from ISS. The SAFESuite family of products performs local and remote vulnerability assessments. RealSecure is an intelligent sniffer that looks for attacks by examining network packets. Beneficial features, such as remote management, consolidated reporting, automated responses, configurable policy templates by target, and secure communications between network console and targets, are available in SAFESuite scanners and RealSecure. These capabilities are found in the NT versions, too.
RealSecure, whether for UNIX or NT, is essentially the same core product. Both versions look for attacks against UNIX and NT systems by tracking network activities. Because network data is the source of information, a vendor does not need a separate analysis engine for UNIX and NT versions of RealSecure. ISS needed only to port the sniffer engine across different OSs. The NT RealSecure product is another flavor of the same solution that is available for a UNIX system running the same product. As you may have noticed earlier, some NT-specific network attacks must be monitored. Both UNIX and NT versions of RealSecure catch these attacks.
SAFESuite products that perform remote scans against NT systems can also be run from UNIX or NT systems because the software is not running on the NT system. Instead, the software is probing the NT target from another node. As in the previous paragraph, specific NT attacks must be tested, whether the console is a UNIX or an NT computer. A SAFESuite local vulnerability assessment tool also is available from ISS. The System Security Scanner (S3) that runs directly on the NT system inspects the system for weaknesses such as weak passwords, registry configuration problems, and other known holes. The Internet Scanner is also available for NT. For a complete list of the attacks that are checked, visit ISS at www.iss.net.
| Previous | Table of Contents | Next |